The age of lugging heavy text books around is now quickly being forgotten(thankfully!) and bright publishers are investing on their own learning management systems (LMS) as a way of managing copy risk, tracking e-resource use and collecting statistics for future development.
Examples:
Most Training Organisations have also embraced e-learning and have their own preferred LMS (ie. Moodle, Janison, Blackboard). We use our LMS to track student enrolments, participation in study, identify problems in learning, track assessments and interactions. This all helps us in meeting our audit requirements.
 In a perfect world we would all have either a Windows or Mac version of e-books and LMSs, but no, there is a Heinz variety out there.
In a perfect world we would all have either a Windows or Mac version of e-books and LMSs, but no, there is a Heinz variety out there.
And not many ‘talk’ to each other. 😦
 The other problem is the re-invention of the resource wheel. If you can’t access a resource already prepared (often at high cost) you need to develop your own (often at higher cost) and protect your own copyright (or, here’s a new concept – share!)
The other problem is the re-invention of the resource wheel. If you can’t access a resource already prepared (often at high cost) you need to develop your own (often at higher cost) and protect your own copyright (or, here’s a new concept – share!)
Resource difficulties aside though, the other issue is the handling of our students’ personal information. As an avid LinkedIn member, this week the issue of protection of personal information really came to my attention with the ‘leak’ of millions of members’ passwords:
http://www.smh.com.au/it-pro/security-it/millions-of-linkedin-passwords-posted-online-20120607-1zx91.html#ixzz1x4owF0iz
If we are using a learning management system outside of TAFE we need to ensure the students are advised of this in the course fact sheet and again in the actual course (that their information is being shared with a third party and why (i.e. to receive a login to the learning). Then we need to carefully structure the lesson plan, to bring the learner ‘back’ into our LMS for consolidation of learning and assessment tasks. Facilitating the learning on someone else’s LMS is another discussion 🙂
The other consideration we need to be mindful of is whether the non-TAFE server that houses this personal data is stored in Australia or not.
For one course we recently put togther with another provider, I followed the Cloud Computing and Privacy Infomation sheets available from http://www.oic.qld.gov.au/information-sheets to advise our students accordingly and restrict access to course material unless the student acknowledges and accepts this disclosure (see below image).

privacy declaration
Who else wants to know?
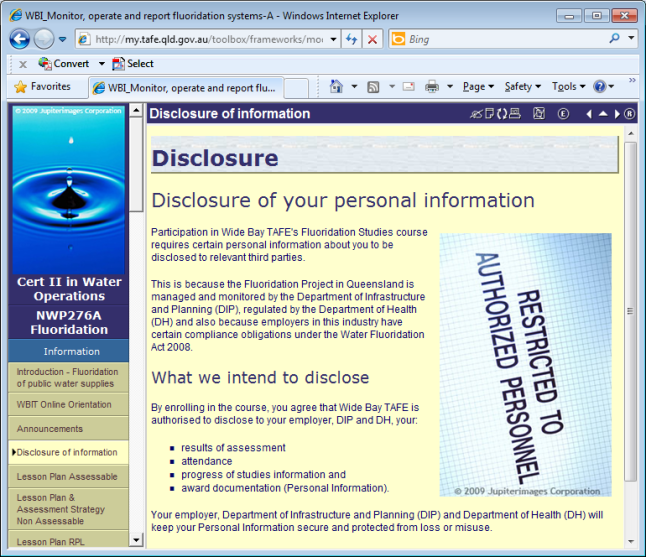
There are other reasons when you will need to advise your student of your intention to share their private information. It could be simply that an employer has paid for a course and wants to know whether his employee has completed the studies successfully (or not). Unless the student is signed up for this study under an Australian Apprenticeship an employer (or anyone else for that matter) doesn’t really have the right to know enrolment details or results unless the student agrees or provides this advice personally. An example below is from our Fluoride training program where successful training is a reportable regulatory compliance item.
Privacy Fluoride






